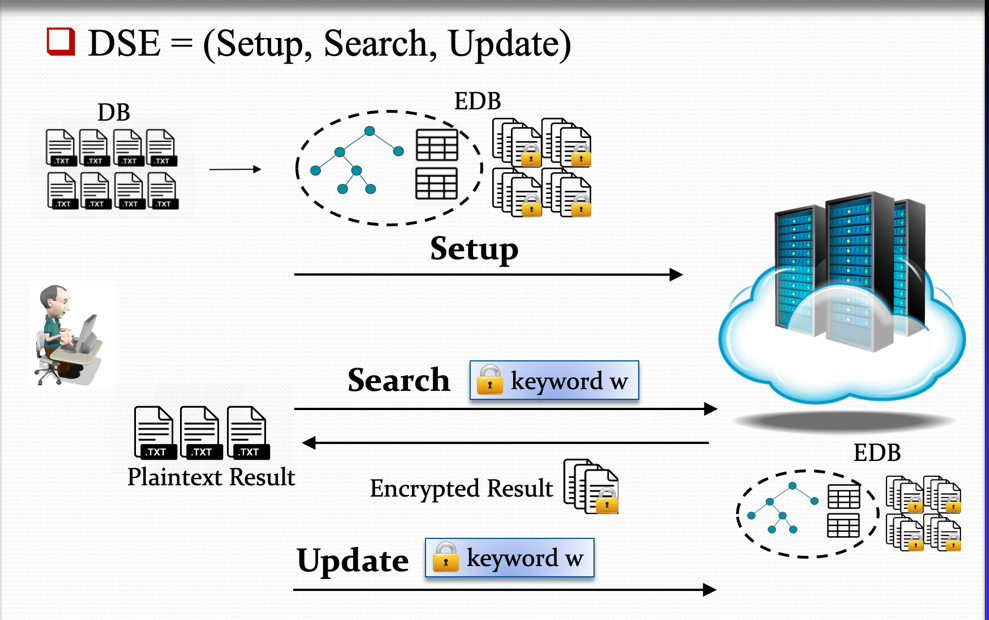
Searching on Encrypted Data
As the demand for cloud computing and cloud storage grows, one of the main considerations has become data privacy, including against the cloud service providers themselves. In particular, the ability to compute directly on encrypted data stored on a remote untrusted server has emerged as a necessary tool. A fundamental task in this area is searching in encrypted datasets. Consider for example a client that owns a database, outsources it to an untrusted server and subsequently issues search queries of the form "retrieve all documents that contain keyword "Test". Ideally, the server should not only learn nothing about the content of the documents (which can be achieved by traditional encryption schemes), but also no additional meta-information, e.g., how many times the keyword was searched for, or the frequency of keywords in the database. The problem is that, since data is encrypted in order to protect privacy, directly searching on it requires novel cryptographic tools.
To that end, Prof. Dimitrios Papadopoulos and his group has proposed multiple novel schemes for Dynamic Searchable Encryption which a family of cryptographic protocols that allow users to upload their encrypted data to an untrusted remote server while maintaining the latter's capabilities to search and update the data. The team has devised novel cryptographic techniques in this direction and has open-sourced several prototype system implementations. The produced results have been published at top-tier computer security venues such as ACM CCS, USENIX Security, and NDSS.
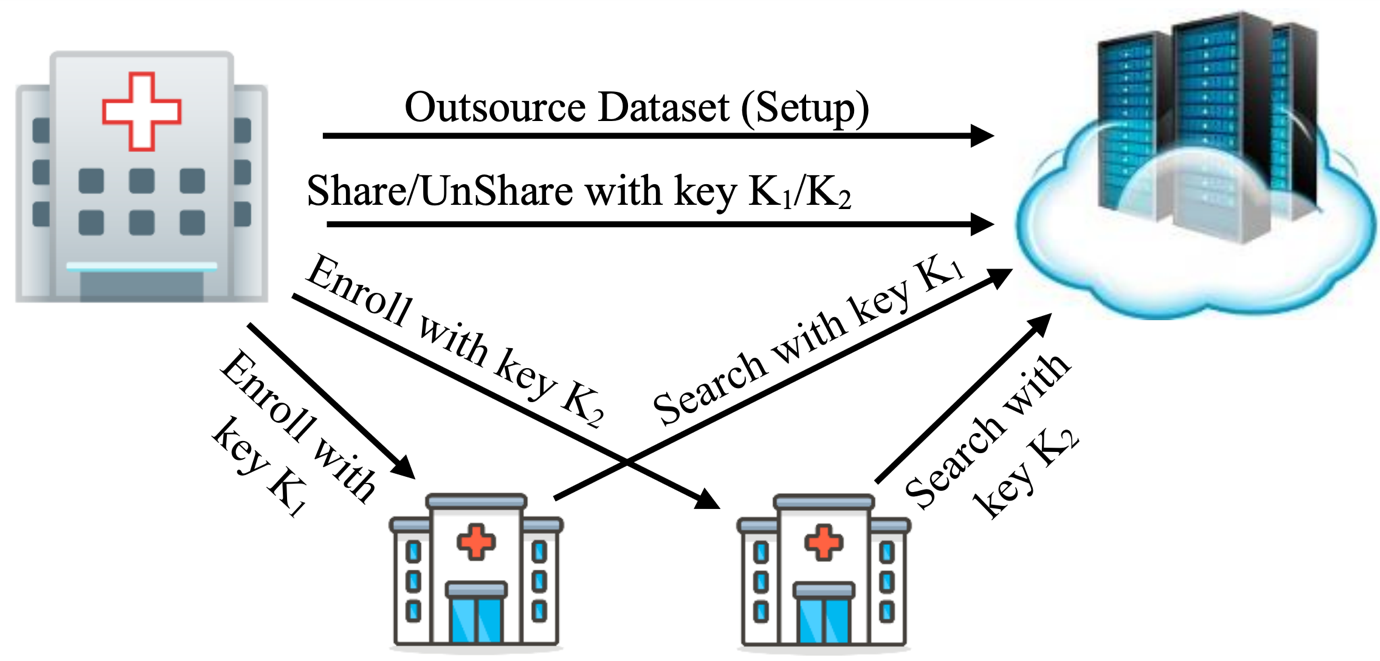
These works span many aspects of Searchable Encryption, such as the following: (1) Securely handling dynamic datasets that support data insertion/deletion/modification without revealing information to the clout provider. Our scheme MITRA is currently the state-of-the-art forward-and-backward private construction in terms of efficiency. (2) Expansion to more "expressive" query types, such as relational database SQL queries with controlled leakage in order to thwart all known attacks. (3) Extension to the multi-user setting where many data owners upload their data to the cloud server and wish to collaboratively share (parts of) it among themselves. This opens up venues towards many real-world applications, such as a scenario where multiple hospitals using a cloud service to selectively share (in a controlled manner) patients' data for subsequent collaboration.
Our lab is currently working on multiple aspects related to searchable encryption such as more efficient systems and TEE-assisted constructions.





 Facebook
Facebook LinkedIn
LinkedIn Instagram
Instagram YouTube
YouTube Contact Us
Contact Us